Built by ethical hackers to secure your future
Protect your digital infrastructure with our cutting-edge cybersecurity solutions, designed to anticipate and neutralize the most sophisticated threats.
Take Your Protection to the Next Level
Security
Security
Get in Touch
Your trusted partner in cyber security
Our certified team uses real-world attack methods to uncover vulnerabilities and deliver insights that boost your security
We help design secure landing zones, assess cloud environments for misconfigurations and threats, and build secure architectures in AWS, Azure, and GCP. Our services include IAM strategy, compliance alignment, data protection, monitoring, and security automation through DevSecOps and IaC best practices.
Ensuring compliance with industry regulations, proactively identifying and managing risks, and enabling strategic, data-driven decisions that support long-term business resilience and accountability
Our mission is to secure the digital landscape


Oktoboot Features
Intelligent threat prediction
Automated penetration testing
Centralized alert tracking
Integration with leading security tools to enhance visibility, automation, and response efficiency
pwn&patch Catalog
Test the security of your network infrastructure against realistic and advanced attacks
Test the security of your network infrastructure against realistic and advanced attacks
Find and fix vulnerabilities in your Web, Mobile and Desktop applications
Conduct gap analysis of your cloud infrastructure.
Design, implement, extend existing security capabilities in the cloud.
Meet regulatory requirements, we provide tailored frameworks, risk assessments, and compliance support to strengthen governance and ensure continuous resilience.
FROM PWN TO PATCH, WE ARE YOUR TRUSTED PARTNER
Certified and experienced consultants
24/7 risk detection
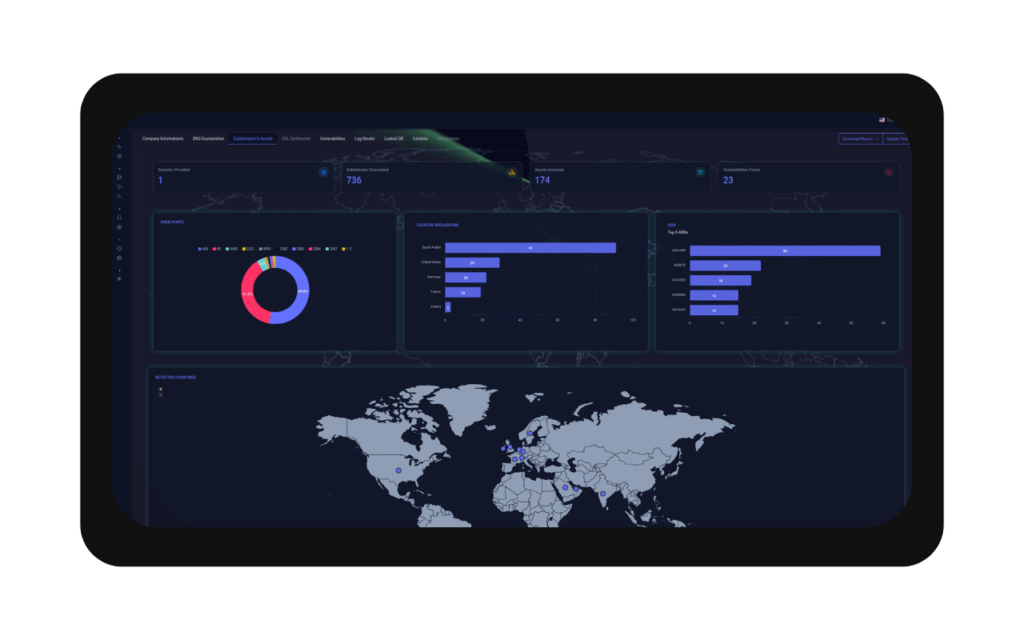
Innovative tools and platforms
100% success rate and the trust of satisfied clients worldwide.
Our certification reflects our commitment to excellence in threat intelligence and data protection
Contact us today for a free assessment of your attack surface.
Got questions?











